Exchange Online announced two important changes on April 15. SMTP AUTH is being depreciated and a new external recipient rate limit is being introduced. The changes are intended to improve the security of Exchange Online. The introduction of an external recipient rate limit is also intended to reduce the ability of spammers to abuse the platform.
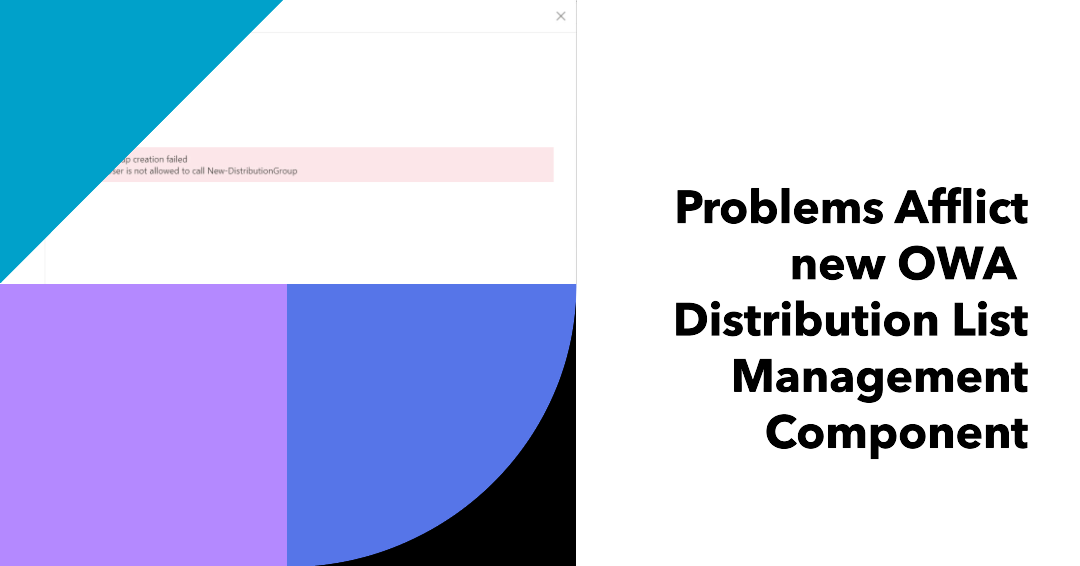
Microsoft announced a new component for OWA distribution list management but clearly the engineers never took role assignment policy customizations into account. If they had, they wouldn’t have created something that ignores the way organizations block end user ability to create new distribution lists. It’s just a sad indication of Microsoft’s attitude to one of the workhorses of Exchange.
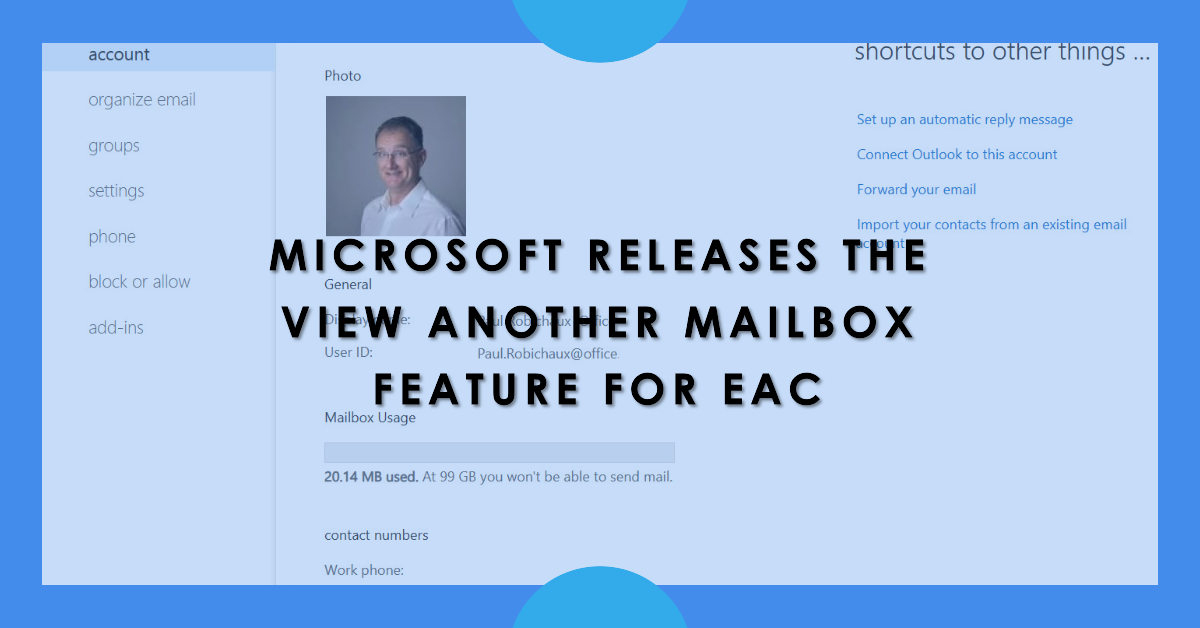
Microsoft has released the View Another Mailbox feature for the new EAC. This is part of the build-out of the new EAC functionality before the retirement of the old EAC. Interestingly, the new feature depends on the old Exchange Control Panel dating back to Exchange 2010. Things aren’t quite as modern and fast as Microsoft says they are.
The Office 365 for IT Pros team welcomes Michel de Rooij as a new author. As a PowerShell Pro, he’ll like the code to update the impersonation protection list for anti-phishing policies. Or maybe he’ll rewrite it to make the code better. Either way, we win and the Mail Flow chapter should get a new lease of life.
A question asked if it’s possible to hide individual distribution list members. It’s easy to hide the complete membership but not as simple to hide just a few. However, an old technique dating back to the early days of Exchange Server works. Sometimes the old tricks are the best!
Microsoft is changing the way that Exchange Online address book updates work to force users to use search rather than browsing through the GAL/OAB. That’s fine and should improve things. When playing with finding how many items are in the GAL, I found that the Get-MgDomainNameReference cmdlet appears to have some issues. First, it can only return up to 999 items, which isn’t a lot when you’re dealing with users and groups that have a connection to a domain. Second, it doesn’t return a nextlink, so you can never fetch all available items. It just goes to prove that Microsoft Graph PowerShell SDK cmdlets are at the mercy of the underlying APIs.
In message center notification MC703706 Microsoft announces yet another attempt to retire the Search-Mailbox cmdlet. This time it’s due to happen in March 2024. I don’t mind Microsoft removing old technology from its products, but it’s important that the old functionality is replaced by newer, better technology. And that’s not the case here. At least, not so far.
For whatever reason, it’s not possible to update the Default MRM policy to add the DeletedItems retention tag to process items in the Deleted Items folder. All attempts to add the tag fail and Exchange Online doesn’t signal any errors. Is this part of Microsoft’s cunning plan to prompt tenants to use Microsoft 365 retention?
Exchange Online keeps message trace data online for 10 days and that’s what’s normally used to check for unused distribution lists. Checking over 90 days is obviously much better, and we can do this by checking against historic message trace data. All explained here with a script to do the job.
Not everyone likes to respond to email with an emoji, which is why the options to disallow Outlook reactions through clients or mail flow rules exist. Everything revolves around the x-ms-reactions message header, which is what Exchange Online uses to understand if people can respond to email with emojis.
Exchange mailbox statistics reports are usually produced using PowerShell cmdlets. However, using Graph usage data is a faster way to process mailboxes because it avoids the need to fetch mailbox statistics by running a cmdlet for each mailbox. This article describes how to speed things up in a way that will probably benefit larger organizations most, but every Exchange Online tenant can probably benefit.
This article explains how to use PowerShell to report the email proxy addresses assigned to Exchange Online mail-enabled objects. Creating the list is straightforward, but figuring out how to use the list afterwards might need more creativity. To get things going, we show how to load the list into a hash table to resolve email addresses into display names.
The Exchange Online developers issued three recommendations to improve performance and reduce memory consumption for Exchange Online PowerShell sessions, specifically those used by automated scripts that don’t involve human interaction. I think two of the recommendations are very practical and worth implementing by everyone, even if you think everything is good with PowerShell.
A new Exchange Online organization setting postpones the implementation of roaming signatures for Outlook clients in a tenant. The setting only allows a postponement because Microsoft really wants all Outlook clients to use the signature data stored in user mailboxes. The extra time allows tenants that use PowerShell to manage OWA signatures to work as they did before roaming signatures came along and screwed things up.
The MFCMAPI utility is of great help to Microsoft 365 tenant administrators who want to understand the data apps store in Exchange Online mailboxes. An on-premises mailbox stores email data, but in the cloud, Microsoft 365 apps use Exchange Online as a convenient place to store data that needs to be accessible to services like Search and eDiscovery.
Like any mail-enabled object managed by Exchange Online, distribution list proxy addresses determine if Exchange can deliver messages to an object. Sometimes the proxy addresses aren’t correct or need adjustment, such as in the case when an organization wants to make sure that all distribution lists have primary SMTP addresses from a specific domain. This article explains how to use PowerShell to adjust the primary SMTP address when necessary.
An old script created to report quotas for user mailboxes provided the basis for email-based reporting of shared mailbox quotas. The old script used just Exchange Online PowerShell. This versions mixes Exchange Online and the Graph SDK and throws in some certificate-based authentication to boot to allow the script to send email from something other than the signed-in account.. It all comes together, using chunks of code from other scripts to speed up writing. It’s the PowerShell way…
After writing a previous article about using PowerShell to analyze message trace data, I was asked about analyzing user (or mailbox) sending patterns to discover who’s sending email and where they’re sending messages to. As in many similar situations, PowerShell is a great tool to use because of its flexibility. This article explains how to generate a per-mailbox report of how many messages are sent and the percentage of internal versus external, plus the external domains the email goes to.
On September 19, 2023 Microsoft announced their intention to retire the Exchange Web Services API on 1 October 2026. The suggested replacement is the Microsoft Graph API. Microsoft acknowledges that some gaps exist that they need to close before EWS retirement happens, but one big issue they didn’t discuss is what happens to the backup products that currently use EWS to backup Exchange Online.
This article describes how to use PowerShell to extract and analyze Exchange Online message trace data to figure out the volume of traffic to outbound domains and from inbound domains. You might think that this is the same information as available in the Exchange admin center mail flow report, but it’s not. Once again, the value of PowerShell in retrieving and using data is evident.
Exchange retention tags can be assigned to mailbox folders. In this article, we explain how to retrieve details of folder and personal tags assigned to folders plus the default archive and delete tags defined in the mailbox retention policy. We also explore if it’s possible to report retention tags assigned to individual messages and conclude that it’s not worthwhile.
At the Inspire conference, Microsoft briefed their partners about the Microsoft 365 Backup and Microsoft 365 Archive products they plan to launch at some time in the future. Microsoft’s biggest advantage is their access to data and the speed at which they can process the information. Whether this gets people past the “all digital eggs in the Microsoft basket” issue remains to be seen.
It would be nice to report that Microsoft’s new My Groups page delivers great user-centric group management portal, but it doesn’t. My Groups can’t deal with distribution groups (lists), which is surprising because distribution lists are a valid Azure AD group type. What’s worse is that the OWA option to manage distribution lists doesn’t work any more. There’s little evidence of Microsoft joined-up thinking here.
Sometimes administrators need to intervene and cancel meetings on behalf of users. That’s why the Remove-CalendarEvents cmdlet exists. The cmdlet scans a user mailbox to find meetings organized by the user for a defined period and cancels the events. Meeting participants receive a cancellation notice. It’s a useful cmdlet to know about, just in case.
Microsoft is making a bunch of subtle tweaks to how Exchange Online MRM processes Purview labels for items moved to the Deleted Items folder. The changes make sure that settings in Purview retention labels are respected better by Exchange Online MRM. Like many of the changes made in the area of data lifecycle management, it’s doubtful if end users will notice, but smart administrators might!
Microsoft has announced that in Fall 2023 they will force Exchange Online users who run unsupported browsers to use OWA Lite instead of OWA Premium. The restriction will start rolling out in September 2023 and be implemented worldwide by November. People who use browsers like Opera and Brave will be affected and be forced to use Chrome, Edge, or Firefox (or Safari on macOS) to use OWA Premium.
Exchange Online organizations configured with multiple geos (satellite regions) still find it problematic to search for mailbox audit events. Microsoft might have fixed the problem for admin audit events, but mailbox audit events are often more important.
Microsoft has decided to push the final deprecation of client access rules to September 2024. However, only rules that can’t be migrated can be used until then. All other client access rules will stop working in September 2023. Microsoft isn’t clear about what technical limitations might allow rules to work for the extra year, nor do they say how tenants can check except by “opening a support ticket.” Although it’s good to move to conditional access policies, Microsoft really could communicate better.
Microsoft’s plan to stop Exchange Online accepting email from unsupported Exchange Servers caused a lot of fuss and bother. Looking through the commentary and questions about the announcement, I’m not sure if people understand fully what’s happening. It seems clear to me, but as Richard Campbell of RunAs Radio fame wants me to rant about the topic, here’s my measured opinion (not a rant).
Microsoft uses machine learning in Outlook and Exchange Online to create the basis for what they call intelligent technology like suggested replies and text prediction. To generate the language models used to figure out how Outlook should respond to users, Microsoft needs to copy data from user mailboxes for processing. The data is removed and the results stored in user mailboxes once processing is complete. Is this an issue for Microsoft 365 tenants? It all depends on your view of how data should be processed.
Mail contacts have long been used by Exchange organizations to provide an identity for external people. Contacts show up in the GAL to make it easy for users to send messages to external people and they can be included in distribution lists. The downside is that mail contacts are only available to Exchange Online. Perhaps the time is right to consider switching focus to Azure AD guest accounts? We explore the option here.
The Test-Message cmdlet is a useful tool to check if Exchange transport rules and DLP policies work correctly. You can input a test message to see what happens as the Exchange transport service applies transport rules, DLP policies, and auto-label policies based on the message contents and properties. Nice as it is to have the Test-Message cmdlet, human knowledge of what transport rules should do is probably an even more important asset.
Exchange Online will create a new inbound connector but won’t activate it until the tenant gives a business justification to Microsoft Support. The restriction applies only to tenants created after January 1, 2023. Microsoft isn’t saying why they implemented the restriction, but it’s likely because of a security concern. In any case, the deafening silence from Microsoft has left ISVs that depend on inbound connectors in a very bad place.
Microsoft announced that the new Message Recall feature is rolling out to tenants worldwide. They hope to increase the success rate for recalls imitated by users from 40% to 90%. Significant limitations exist. Message recall only works from Outlook for Windows and recall can only handle messages that remain within the same Exchange organization. Even so, the prospect of a huge improvement in the success rate will make the new feature very attractive to the people who really need to recall a message.
Room mailboxes are still heavily used for in-person meetings. It’s good to know how often and when rooms are used, which is why we have the room mailbox report script. In the second version of the script, we include code to figure out the daily usage pattern of individual rooms and for all rooms across the organization. The graphics in our bar chart are crude, but the chart is generated with a few lines of PowerShell, so feel free to improve the script.
Microsoft announced support for concurrent Exchange Online license assignments, aka license stacking. This means that the workload can sort out the capabilities made available to a user through multiple licenses and make the maximum functionality available to the user through whatever’s deemed to be the “most superior” license. If that sounds like so much mumbo-jumbo, it might just be, unless you’ve been plagued by people losing access to their mailboxes because of shifting license assignments in the past. If you have, this change will make you very happy.
Much to our distress, we discovered that the contact form for the Office 365 for IT Pros website was broken. We fixed everything up and use a shared mailbox to receive the contacts logged by people on the website. In fact, we use a distribution list as the first point of contact. Its membership includes the shared mailbox and other user mailboxes. Everything works very nicely now.
Azure AD user accounts and Exchange Online mailboxes share many properties, including some for a user’s address. When it comes to countries, Azure AD has the country property while Exchange uses the CountryOrRegion property. Sometimes the two don’t match up. Why does this happen and does it matter in practical terms? What other country or regional settings exist that need to be managed? A simple question sets off a big discussion.
This article explains how to use PowerShell to enable Exchange Online archive mailboxes after primary mailboxes reach a certain size. Some simple PowerShell code checks the mailbox size and if it’s too large, enables the archive and assigns a mailbox retention policy containing a default move to archive tag to move items from the primary to the archive mailbox. Some Azure Automation would make sure that the script runs periodically to keep mailboxes in good health.
Microsoft announced that they will pause sending the daily Viva Briefing messages to make improvements to the personalized content in the messages. No detail has been revealed about the kind of changes Microsoft is contemplating, so all we can do is write some PowerShell to show which mailboxes are currently enabled to receive the daily briefing.